SlowAES Bypass the test cookie NodeMcu
SlowAES Library for Esp8266 (NodeMCU)
Hello embedded friends, this article is about the web-scrapping protection slowAES (aes.js). If you want to get a web page with nodeMCU HttpClient and your response is different from what you see when browse it a browser and your response like below :
<html>
<body>
<script type="text/javascript" src="/aes.js"></script>
<script>
function toNumbers(d) {
var e = [];
d.replace(/(..)/g, function(d) {
e.push(parseInt(d, 16))
});
return e
}
function toHex() {
for (var d = [], d = 1 == arguments.length &&
arguments[0].constructor == Array ? arguments[0] :
arguments, e = "", f = 0; f < d.length; f++) e +=
(16 > d[f] ? "0" : "") + d[f].toString(16);
return e.toLowerCase()
}
var a = toNumbers("f655ba9d09a112d4968c63579db590b4"),
b = toNumbers("98344c2eee86c3994890592585b49f80"),
c = toNumbers("a76ce883a42eb6e9fff3e05d9cc6c7e5");
document.cookie = "__test=" + toHex(slowAES.decrypt(c, 2, a, b)) +
"; expires=Thu, 31-Dec-37 23:55:55 GMT; path=/";
location.href = "http://www.namazvakitleri.site/i=1";
</script>
<noscript>
This site requires Javascript to work, please enable
Javascript in your browser or use a browser with Javascript support
</noscript>
</body>
</html> Then, this means your page protected by slowaes protection to prevent web-scraping, robot actions.
What is slowAES protection?
When you get that kind of a web page, your browser (if it's your first visit) gets the code above first, and run this javascript code to generate a cookie called __test and some encrypted value in it. This value generally depends on your ip address. And js set this cookie on your browser and redirect browser the page you requested, plus a query string i, or attempt in some systems. The second request done with the cookie set before, server check if the cookie set and correct view the page you actually wanted to see.
How to bypass slowAES by NodeMcu?
First step : get the page with HttpClient
HttpClient http; WiFiClient wfc; String web = "http://example.com/"; http.begin(web,wfc); String payload = http.getString();
then you have the java code like above in payload var.
Second step: obtain a,b,c values in code.
/* getting abc vars */
int loc = payload.indexOf("var a=toNumbers(");
String temp = payload.substring(loc, temp.length());
temp.replace("var a=toNumbers(\"", "");
String a = temp.substring(0, 32);
temp.replace(a + "\"),b=toNumbers(\"", "");
String b = temp.substring(0, 32);
temp.replace(b + "\"),c=toNumbers(\"", "");
String c = temp.substring(0, 32);
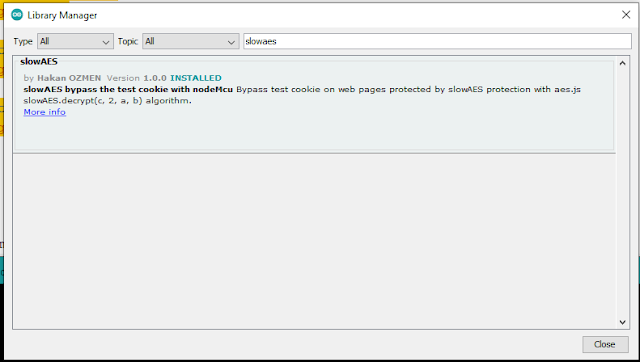
Third step: Installing slowAES library
On the menu click Tools, Manage Libraries..., type slowAES
and click Install.
Fouth step: getting test cookie value with slowAES library.
include the library header file
#include <slowAES.h>
obtaining __test cookie value :
uint8_t aNums[16]; uint8_t bNums[16]; uint8_t cNums[16]; toNumbers(a.c_str(), aNums); toNumbers(b.c_str(), bNums); toNumbers(c.c_str(), cNums); uint8_t finalCookie[33]; slowAES _slowAES; uint8_t resNums[16]; _slowAES.decrypt(cNums, aNums, bNums, resNums); toHex(resNums, finalCookie); String str = (char *)finalCookie;
now you have test cookie's value in str var.
Fifth step: the second call of the page:
web = web + "?i=1";
http.begin(wfc, web);
String fullCookieStr = "__test=" + str;
http.addHeader("Cookie", fullCookieStr, true);
http.addHeader("Host", "www.example.com", true);
http.addHeader("Connection", "Keep-Alive", true);
payload = http.getString();
Serial.println(payload);
That's cool you have the page content in payload variable. You can do what ever you want with it.


Comments
Post a Comment
You can share your experience, or ask anything about the topic, Let's write ;)